On November 30th, 2018, Marriott disclosed its Starwood acquisition had a 4-year-old data breach that exposed data for up to 500 million customers. However, this wasn’t the first time they have been hacked.
Marriott has had a history of cyber breaches:
- In 2015, Starwood Hotels – which Marriott acquired – suffered a malware data breach, which originated from a POS (Point of Sale) systems attack
- In 2017, an ex-employee had access to Marriott’s pricing and reservation system.
Security Vulnerabilities – Threatening the Foundation of Our Digital Economy
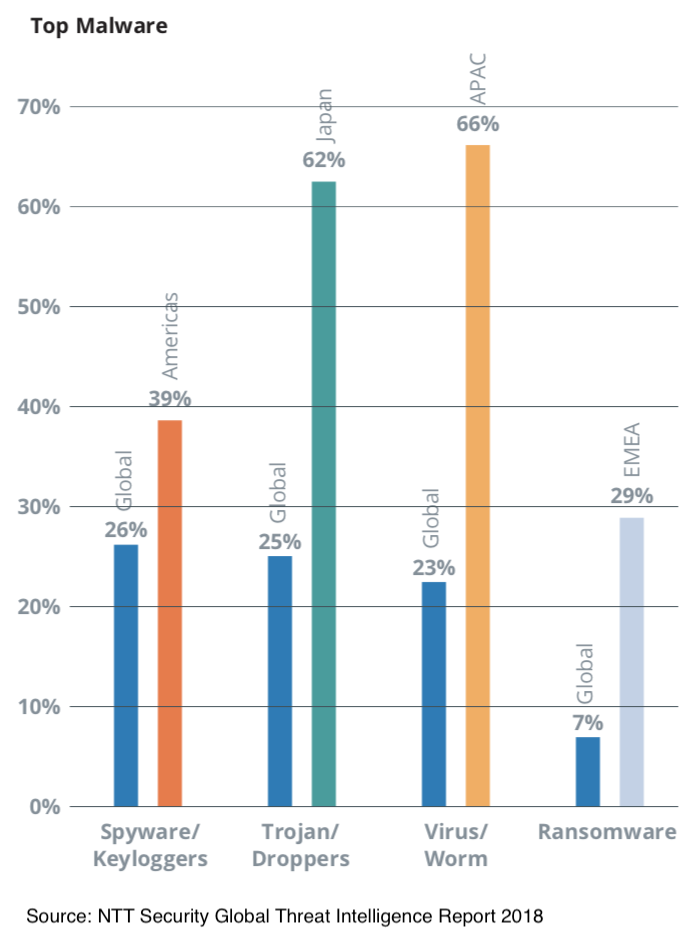
As the digital economy continues to expand its footprint into the lives of consumers, individuals and businesses with POS systems, mobile payment from smartphones, RFID and NFC-based payment systems, we are all exposed to a fast-growing cyber threat landscape that makes personal data increasingly vulnerable to attack due to the generally insecure state of the back office systems, network infrastructure as well as the connected devices used today. According to NTT Security, malware-based attacks continued to increase significantly in 2017 with expectations that the volume of incidents will continue to rise as attackers leverage new technologies to exploit existing and new network and endpoint vulnerabilities.
With a slew of industrial and consumer IoT applications coming out of pilot purgatory and into market, we can expect cyber security threats to increase drastically as data and computing is distributed outside the corporate data center and public clouds into a complex hybrid cloud/edge computing environment that presents a massive attack surface rife with holes. For many leading enterprises, this landscape of cyber risk can span the globe.
Cybersecurity Breaches Are No Longer Back Burner Issues
Enterprises continue to aggressively pursue their digital ambitions and are facing increasing cyber risk headwinds and consequences, especially with what appears to be a global movement toward what we call a Privacy First regulatory environment – most prominently exemplified by GDPR (General Data Protection Regulation), which went into effect on May 25th of this year.
Historically, cyber breaches that compromised consumer personal data had significant financial impact as exemplified by the Equifax hack in August of 2017. During the course of two weeks after the data breach of about 143 million consumer accounts was disclosed Equifax’s stock declined 35.8 percent. Approximately 15.2 million records of UK clients were exposed resulting in a maximum fine of £500,000 under the U.K.’s older privacy laws that predate GDPR.
With GDPR in place, a mishandling of a cybersecurity event that involves the compromise of personal data could result in millions of dollars in fines if not billions. This is a risk that Facebook is facing today with what seems to be a regular stream of revelations of security breaches and consent violations that impact the personal data of its approximately 2.3 billion users. Though the broader market has declined over the past four months, Facebook has suffered dramatic declines in their market cap directly attributable to significant cybersecurity events and revelations over the course of 2018 – such as the Cambridge Analytica debacle.
It is clear that the consequences of cybersecurity hacks are increasing in terms of impact on brand, customer loyalty, shareholder value, and corporate accountability. Digital business can no longer treat cybersecurity as a tertiary agenda item or concern as Wipro’s 2018 State of Cybersecurity Report survey of 203 enterprises indicate that no more than 4% of IT budgets are allocated to cybersecurity.
A New Problem in Need of a New Solution – Cybersecurity in a New Era of Digital
It is clear that as industries and companies continue to become increasingly digital the cybersecurity issue is not going to go away. In fact, it will get more numerous, more complex, more expansive and more consequential. As the nature of cybersecurity continues to morph with increasing velocity and volume, traditional information security disciplines, technologies, processes and solutions will not be sufficient to adequately keep up and secure a digital enterprise.
Digital leaders within the enterprise such as CISOs, CTOs and CIOs need to look at cybersecurity in a holistic way and continue to bridge new digital layers and modules that are continually added to today’s enterprise digital portfolio. These digital leaders need to consider new approaches, technologies and tools to de-risk multi-faceted cyber threats that can range from external attacks from state-sponsored actors to internal breaches from rogue employees or ex-employees. These threats can now come from a much wider range of vulnerabilities from the software level all the way down to the processor in a server sitting in your data center, your 3rd party service provider or public cloud provider.
Mergers & Acquisitions – The Cyber Super Bug
The Marriott data hack put a spotlight on the cyber risks that a company can inherit through an acquired entity, or in any arrangement where there is an ongoing, shared-custodianship of personal data and intellectual capital. In 2016, Yahoo! also showed us that cybersecurity issues can dramatically impact the value of a selling party as it was compelled to lower its sales price by $350 million (7.2 percent discount from original $4.83 billion dollar price) to Verizon due two data breaches that occurred in 2014 – one event that affected approximately 500 million users and a separate incident that impacted 1 billion users.
As Verizon learned mid-transaction and Marriott learn post-merger, cybersecurity and the quality of an entity’s security practices, infrastructure, implementation of tools and people are critical elements that need to be carefully evaluated prior to closing the deal. While anti-malware software can detect a potential attack on a company workstation, smartphone or network, there are no simple solutions or software that can detect what you may inherit through the acquisition of a foreign digital portfolio (IT + OT + IoT).
Executive teams, executive boards and digital leaders need to consider a new model and approach of digital business due diligence that incorporates a significant focus and investment in vetting the cybersecurity posture and health of an acquisition target as well as one’s own enterprise. Traditional approaches to information security will not be sufficient.
New Digital Governance for New Digital Realities and Threats
According to a recent NACD survey of board directors, only 12% of boards have evaluated the cybersecurity consequences of major strategic decisions. It is clear that new governance mindset, model and discipline are needed to bring focus, knowledge and effective processes to the oversight of holistic enterprise security and trust in today’s corporate board rooms. The Marriott hack is a sobering indicator of this dire need for corporate boards and executive teams to take cybersecurity very seriously.
Do you have clear ownership and accountability defined for the company’s digital strategy and security? Is the assigned cybersecurity owner equipped with the tools and the competent resources they need to effectively manage cyber risk for the enterprise and can they evolve defenses as the business continues its digitization and transformation? Is the board ready to support the executive team in managing a security incident and administering the communications to the investment and regulatory communities to minimize financial and fiduciary damage to the company? Is cybersecurity a primary agenda item on your board agenda? If the answer to any of these questions is “no” you have some work to do.
Implications for Business Leaders
The C-Suite and the corporate board need to understand the significant risks that the fast-changing and evolving digital security threats will have on their business and on their digital strategy. Billions of dollars in regulatory fines, market valuation losses, as well profound loss of customer loyalty and trust are the emerging and intensifying consequences of cyberattacks. Not only does a corporate board need to be the custodian of the digital security of the company that it governs, it must ensure holistic due diligence of the digital security posture and quality of any company that it considers acquiring.
Enterprise CISOs, CTOs and CIOs need to think of security holistically and consider new approaches to address an expanding field of threats like server sabotage, POS hackings, and rogue employee insider threats as well emerging external threats that will come with IoT deployments. The management of risk will require ensuring that both internal and external resources and infrastructures are fully vetted whether they are enterprise-managed or managed by a 3rd party service provider or outsourced to 3rd party systems integrators. This diligence is especially vital in the context of M&A.
Technology vendors have an opportunity to connect the dots and bridge existing and emerging technologies into a holistic security platform that incorporates virtual solution architectures, privileged access management, AI-based behavioral analytics and DPI/DLP (Deep Packet Inspection/Data Loss Prevention) solutions, with continuous monitoring and reporting in place. Traditional ICT vendors and service providers will need to venture outside of their silos and work together with enterprise CISOs/CIOs/CTOs in designing and deploying innovative new solutions to counter the continuous onslaught of cyberattacks and new forms of threat that will accompany the global digital race.
Contact us if you would like to discuss how neXt Curve can provide you with insight into emerging governance practices, technologies and holistic security solutions that could be critical in the secure governance of your digital enterprise.
Related Content & Media
- The Digital Gap: Boardroom Leadership & Governance
- Market Insight: Holistic Security is Key to Meet the Digital Security Threats of Today & Tomorrow
- Market Insights: Another Intel Security Flaw? How This Foreshadows Delays for 5G
- Contextually-Aware Mobile Security as a Service: The Key to IoT Security and GDPR Compliance & Readiness with Blockchain
by
Akshay Sharma
Research & Advisory Fellow, neXt Curve
and
Leonard Lee
Managing Director, neXt Curve
December 3, 2018
© 2018 neXt Curve. All rights reserved.
2 comments